Having a proxy is essential whether you are browsing the web for social or business reasons. It allows you to establish a secure and an indirect connection to different locations on your mobile device or via your PC. It is an application that allows you to have a seamless connection to another network. The beauty of proxy is that you can keep your information private, it filters traffic and directs you to the ideal or correct server.
When you buy proxies, you can always enjoy a secure connection to the desired network. Apart from keeping your information private, proxy increases your browsing speed, enhances your security and blocks any suspicious websites. With this in mind and with the fact that there are different proxies, here is a guide to help you decide which proxy you should buy.
Which Proxy You Should Buy
Anonymous Proxy
Anonymous proxy servers work by masking your IP address and uses a unique one. It allows you to protect and conceal your identity. When using an anonymous proxy, you can access different restricted websites.

Transparent Proxy
Transparent proxy servers do not enforce any local policies. It performs the basic proxy functions without adding, removing or changing any information or attributes it comes across. Typically, this is used to catch websites but it doesn’t guarantee high levels of anonymity.
With a transparent proxy, you can work around any IP ban. This means that you do not necessarily have to configure your web browser in any special way to use the proxies.
High Anonymity Proxies
The high anonymity proxy servers do not reveal your IP address at any given point. It uses your IP address with a REMOTE-ADDR header. As such, you will appear as the actual proxy server client.
Distorting Proxy Server
Distorting Proxy Server always performs basic proxy functions. Your target websites will know that you are using a proxy. Even so, it conceals your identity by faking your target connection. Therefore, it will not be recognized as your IP address.
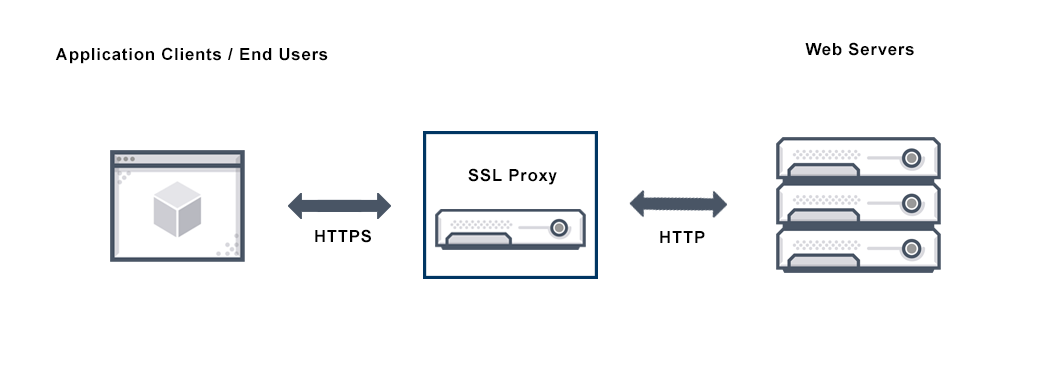
SSL Proxy
Secure Sockets Layer proxy protects your data during a connection or a transmission. It is useful when performing a transaction because it uses the https symbol. Naturally, SSL proxy acts as a connection between you and the receiver thus, protecting your server from possible hackers.
File Transfer Protocol Proxy
FTP protocol proxy is used in an array of applications. When building a website, this is a useful proxy. It is an advanced proxy that guarantees a high level of security whenever you are uploading your files to a different server. The proxy offers different encryption methods and a cache function that makes your browsing process safe, reliable and secure from hackers.
HTTP Proxy
HTTP Proxy offers easy access for catching of different files and web pages. Therefore, it becomes easy for you to transfer them safely. Today, many browsers will cache your frequently visited pages using an HTTP proxy.
SOCKS Proxy
Socks proxy server helps you to establish a secure connection through the exchange of messages. It gets the mechanism that works through an IP that further deploys a firewall to keep your data private.
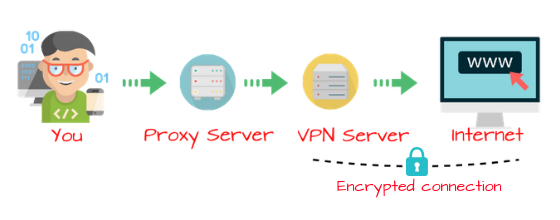
Intercepting Proxy
The Intercepting Proxy is a reliable proxy that works with a gateway. With this proxy, connections are made from your browser through a given gateway. It is then directed through the proxy without a configuration from your clients’ end. The proxy is generally detected on the HTTP header on the server.
These are generally some of the best proxies you can buy. However, there are still many other types that you can settle for online. Before you use any, it is crucial that you carefully review your options. Determine whether you need a shared or a dedicated proxy server. Each of these comes with different levels of security guarantee and privacy. Go for what appeals to your browsing needs.
Leave a Reply